Social media remains fertile ground for hackers to expand their attacks through malware and trendjacking.
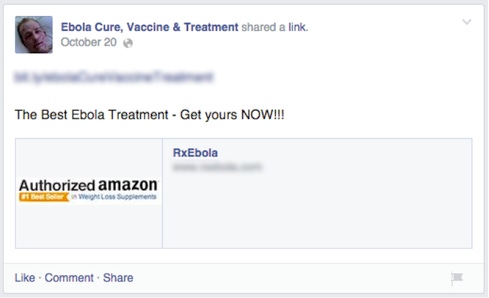
The past several weeks have seen numerous articles about the spread of malware via fake Ebola-related emails. Hackers will imitate the CDC, WHO, or major news outlets like CNN to spread dangerous links. Shocking headlines -- "Ebola virus has been cured!" -- entice people to click, resulting in compromised devices and accounts.
The ploy is not limited to email. Social media have also been used to disseminate dangerous information and manipulate users following the Ebola story. Hackers append trending hashtags, most commonly #Ebola, to amplify the scope of their attack -- a tactic known as trendjacking.
[Social networks can be both hero and villain during public panics. Read #Ebola Lessons: How Social Media Gets Infected]
By attaching an unrelated hashtag on to their own content, hackers capitalize on the popularity of the hashtag to target a larger audience. Users looking for information on social media need to be vigilant. The following precautions will help you avoid malicious links on social media.
Check the profile
The posting profile can be a revealing element in the equation of social media safety. Hackers will often use botnets (large networks of automated accounts) to spread malware and repost content. Bots are frequently programmed to trendjack popular hashtags, such as #ebola. The following features are common botnet giveaways:
Strange or randomly generated handles or usernames
Bursts of posts with links followed by bursts of posts with text only. This is done to fly under the radar of a social network's terms of service.
Posts and account descriptions are book quotes or pseudo-coherent, which indicates an algorithmically generated strings of words. If the posts don't quite make sense, there's a good chance they are being computer generated.
Questionable account pictures, like a scantily clad woman, are often used to catch the eye and entice users to interact with the account.
Check the post
The content in the post itself can be a strong indicator of a malicious link.
If the post contains sensational text -- like a too-good-to-be-true statement or an incredible headline -- it's likely clickbait.
If the post is affixed with unrelated hashtags, the hacker is likely using spray and prey distribution tactics. This type of trendjacking broadcasts the post to as large an audience as possible. Avoid these URLs, as they likely contain phishing or malware.
Check the link
Generally, link analysis requires advanced algorithms that analyze for hundreds of threat attributes. However, there are a handful of things you can do manually to identify malicious links.
Always hover over a link before you click. A preview of the link will appear that will show the full address, unless it is a shortened link.
Link shorteners, such as Bitly, are often used to hide a malicious link. For social networks with character limits, like Twitter, shortened links are common, so it is especially important to use discretion. Use a free link lengthener (like longurl.org or unshort.me) to reveal the full URL.
Be wary of extremely long or random-looking links. These links are often used to disguise a malicious destination.
Watch out for URLs that contain almost the same characters as real sites but are one or two characters off.
Scan the link using any free online link analyzer, such as scanurl.net or virustotal.com.
When in doubt, don't click
If you doubt a link is trustworthy, don't risk it. There is plenty of quality literature on the web about events like the Ebola epidemic, and you can find it safely by searching directly. Don't get caught up in the panic on social media -- you'll save your devices and accounts from being infected, as well.
Malicious software is morphing to be more targeted, stealthy, and destructive. Are you prepared to stop it? Get the Malware Mutation issue of Dark Reading today.
About the Author(s)
You May Also Like







