Security researchers from Check Point plan to disclose a flaw at the Black Hat Asia conference which they claim endangers the way mobile device management software interacts with iPhones and iPads. Check Point calls the vulnerability "SideStepper" because it sidesteps the normal app approval process.

10 Windows 10 Hacks To Maximize Your Experience
10 Windows 10 Hacks To Maximize Your Experience (Click image for larger view and slideshow.)
While Apple tries to identify the vulnerability that allowed the FBI to access an iPhone used by one of the San Bernardino shooters last December, it may have another hole to find.
At Black Hat Asia on Friday, security researchers from Check Point plan to disclose a vulnerability that could allow an attacker to hijack iOS devices tied to enterprise mobile device management (MDM) software. On Thursday, the company published a whitepaper outlining the issue.
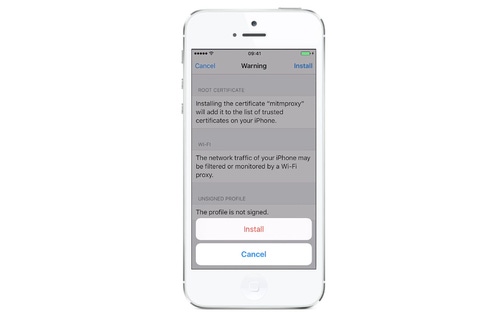
To exploit the flaw, an attacker would have to dupe an iOS user into installing a malicious configuration profile on his or her device, something that can be accomplished through a phishing attack.
As Apple sees it, this isn't an iOS issue. "This is a clear example of a phishing attack that attempts to trick the user into installing a configuration profile and then installing an app," an Apple spokesperson said in a statement emailed to InformationWeek. "This is not an iOS vulnerability. We've built safeguards into iOS to help warn users of potentially harmful content like this. We also encourage our customers to download from only a trusted source like the App Store and to pay attention to the warnings that we’ve put in place before they choose to download and install untrusted content."
An iOS configuration profile is an XML file that can be used to distribute custom device settings related to networking, certificates, policies, and authentication. MDM software puts iOS devices under the control of IT administrators through the application of these profiles.
Configuration profiles have long been known as a potential avenue for man-in-the-middle (MitM) attacks. In 2013, Ohad Bobrov, then CTO of Lacoon Mobile Security, wrote about the potential weakness of configuration profiles on Check Point's blog. Evidently convinced that what Bobrov described as iOS's Achilles' Heel could add value to its mobile security offering, Check Point acquired Lacoon in 2015.
The same year, another mobile security firm, Appthority, disclosed an enterprise iOS vulnerability called "Quicksand." That flaw exposed sensitive MDM configuration and authentication information that should have been rendered inaccessible though app sandboxing. Apple patched Quicksand in iOS 8.4.1.
In a phone interview, Michael Shaulov, head of mobility product management at Check Point and the former CEO of Lacoon, said he was aware of five or six attacks that have exploited enterprise access to iOS in the past few years.
While the potential fragility of the enterprise pathway into iOS isn't new, the specifics are. Check Point researchers found a flaw in the way iOS devices communicate with MDM software that can be used to push malicious enterprise apps onto iOS devices as over-the-air updates, without seeking user or administrator consent.
Check Point calls the vulnerability "SideStepper" because it sidesteps the normal app approval process. Shaulov estimates that tens of millions of devices under enterprise management may be vulnerable.
Because the Apple Developer Enterprise Program allowed companies to "bypass the App Store review process," said Shaulov, "it became a straightforward way for hackers to introduce malware without jailbreaking."
Apple partially addressed this problem with the introduction of iOS 9, by requiring more user interaction when installing enterprise iOS apps from links. But, according to Shaulov, it didn't harden the MDM app installation process.

Are you prepared for a new world of enterprise mobility? Attend the Wireless & Mobility Track at Interop Las Vegas, May 2-6. Register now!
"MDM communication is basically prone to a MitM attack, which could allow an attacker to issue fake commands from MDM software to a device to force the sideloading of an app," said Shaulov.
The reason for this, said Shaulov, is that MDM communication in iOS isn't protected by SSL Pinning.
Shaulov argued that Apple is too quick to dismiss the attack. "While we respect Apple's work in the area of mobile security, calling SideStepper just a phishing attack misrepresents the overall magnitude of the vulnerability," he said in an email message to InformationWeek. "Getting a user to install a malicious configuration profile on an iPhone or iPad using a phishing attack is pretty simple. Even with warnings, the typical user will tap away until the profile is installed."
Shaulov says SideStepper can be used to circumvent the work Apple has done to protect customers from malicious enterprise apps. "With this vulnerability, not only can attackers install malicious apps over-the-air, they're doing so in a way that's totally trusted by iOS and the user," he said.
By default, iOS doesn't allow apps signed with untrusted certificates to run. However, a proof-of-concept video provided by Check Point showed a generic warning panel that could be dispensed by two clicks on "install" buttons after a user follows a text message phishing link. The process depicted was routine enough that it could easily dupe someone.

(Image: Mutlu Kurtbas/iStockphoto)
Coincidentally, Check Point claims that its Mobile Threat Protection (enterprise) and ZoneAlarm (personal) software can mitigate the threat.
Shaulov said Check Point informed Apple of the vulnerability in October 2015 and has yet to hear anything about plans to address the flaw. Apple's statement suggests it doesn't see the issue as critical.
Apple has a reputation for being slow to respond to security issues. And it's been thus for almost a decade. At the same time, other companies, like Microsoft and Oracle, have been subject to similar criticism. And even Google, known for advocating more responsive disclosure, has been taken to task for being slow to fix bugs.
There is one clear way that Apple differs from other technology companies. Unlike Facebook, Google, Microsoft, and other organizations with formal bug bounty programs, Apple rewards vulnerability disclosures with public acknowledgement rather than monetary recognition.
Yet, the fact that Apple actually responded to Check Point's claims diverges from a long tradition of silence about security issues. This may be a consequence of CEO Tim Cook's decision to make security paramount for the company following its brief but intense legal battle with the FBI. Or it may be the way that the company handles security claims it sees as exaggerations. Back in 2006, Apple challenged a SecureWorks demo at Black Hat USA over claims related to its MacBook.
Black Hat is produced by InformationWeek's parent company, United Business Media.

About the Author(s)
You May Also Like







