Media freedom group GreatFire.org claims Apple's iCloud is being subject to a man-in-the-middle attack by China's censorship apparatus.

Apple iPad Air 2: Visual Tour
Apple iPad Air 2: Visual Tour (Click image for larger view and slideshow.)
Apple's iCloud service is being subjected to a man-in-the-middle attack by authorities in China, according GreatFire.org, a website that monitors censorship in China.
Based on technical information posted on GreatFire.org, it appears that China's security apparatus is employing a fake Apple certificate to intercept iCloud data traffic.
"This is clearly a malicious attack on Apple in an effort to gain access to usernames and passwords and consequently all data stored on iCloud such as iMessages, photos, contacts, etc," GreatFire.org wrote Monday on its website. "Unlike the recent attack on Google, this attack is nationwide and coincides with the launch today in China of the newest iPhone."
In order for a web browser to know whether a website is what it claims to be, it relies on a certificate issued by a certificate authority, a third-party organization that vouches for the website through a cryptographic signature. Fake certificates, however, can be obtained, illicitly or by lawful process.
[Want to try out Apple's new mobile payments service? See Apple Pay: Where To Use It.]
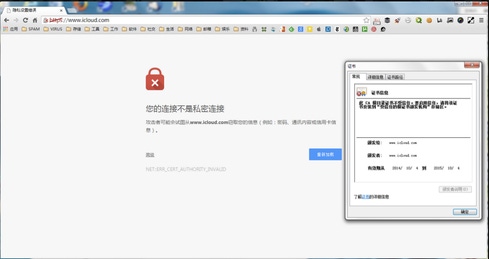
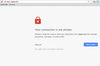
The alleged attack appears to be affecting access to Apple's website in the US, at least in the Google Chrome browser. Attempting to visit Apple.com on Monday morning Pacific Time using Chrome presented a security warning, "Your connection is not private," and an error string referring to an invalid certificate authority.
Google did not immediately respond to a request to explain the warning for visiting Apple's website in the US using Chrome. Github, Google, Microsoft, and Yahoo have also been subjected to similar attacks in China.
According to GreatFire.org, both Chrome and Mozilla Firefox will try to prevent users from accessing websites with forged certificates. However, Firefox did not suggest anything was amiss when accessing Apple's website in the US.
Apple did not immediately respond to a request for comment.
The alleged attack comes following Apple's claims last month that it has never created a backdoor in its products to provide government authorities with access. Apple also said it cannot decrypt data on iOS 8 devices, regardless of government demands.
In the US, Apple's claims about the security of data on iOS devices have prompted FBI Director James Comey to call for an update to the 1994 Communications Assistance for Law Enforcement Act (CALEA) to ensure authorities can access encrypted data on devices. The security industry calls this a backdoor; Comey insisted, "We are not seeking a backdoor approach."
In China, Apple's security claims appear to have elicited a different response. GreatFire.org speculates that the man-in-the-middle attack may reflect the security in the new iPhone, which just became available in China. By gathering Apple IDs and passwords, Chinese authorities would have an easier time unlocking encrypted data on iOS devices.
"When details of the new iPhone were announced, we felt that perhaps that the Chinese authorities would not allow the phone to be sold on the mainland," GreatFire.org says.
The website noted that while it's not clear whether Apple altered the iPhone in mainland China to accommodate authorities, the man-in-the-middle attack suggests tension with Chinese authorities.
Considering how prevalent third-party attacks are, we need to ask hard questions about how partners and suppliers are safeguarding systems and data. In the Partners' Role In Perimeter Security report, we'll discuss concrete strategies such as setting standards that third-party providers must meet to keep your business, conducting in-depth risk assessments -- and ensuring that your network has controls in place to protect data in case these defenses fail. (Free registration required.)
About the Author(s)
You May Also Like







