Our new survey shows fed agencies focusing more on security, as they should, but they're still behind the times with cloud use, data center consolidation, and overall innovation.
 Get the August issue of InformationWeek Government
Get the August issue of InformationWeek Government
If government ITprofessionals aren't getting much sleep these days, it's likely because they're more worried than ever about catastrophic cyber-security breaches.
In InformationWeek's 2014 Federal Government IT Priorities Survey, 70% of respondents said that cyber- and information security programs are "extremely important" at their agencies, making IT security the highest government IT priority. Another 24% said IT security is at least fairly important. Only 3% said security is "not important at all."
The survey also demonstrated that security is intensifying as the top government IT priority. In last year's survey, 67% of respondents stated that information security is extremely important.
But while our survey indicates that government agencies have a sharp eye on information security, they're falling behind in critical areas such as cloud, data center consolidation, and overall IT innovation.
Protecting Information Gets Complex
Beyond high-profile incidents like the Edward Snowden leaks of NSA documents, government IT pros are understandably troubled by the tens of thousands of cyber-attacks by foreign hackers on government systems and the new risks created by the proliferation of mobile devices. Another source of concern: unnoticed security breaches. A report issued earlier this year by Sen. Tom Coburn, R-Okla., found that nearly four in 10 intrusions into major civilian agency systems go undetected, posing a nightmare for IT managers.
"Information is the new weapon of choice," says one respondent to our survey, Joseph Reddix, CEO of the Reddix Group in Hanover, Md., which supplies IT project management and capital planning services to federal agencies. "When information is weaponized, you're in trouble. Information technology is about information, and it really should be about secure information."
But protecting information is becoming increasingly complicated. "If a foreign national stole plans for the F-35 [fighter plane], which is made in 40-plus different states," Reddix explained, "you only need one part to go bad to cause some big problems. And considering the planes cost $300 [million] to $400 million each, that's an awful lot of money. It can be extremely costly when there's a security breach."
Figure 2: 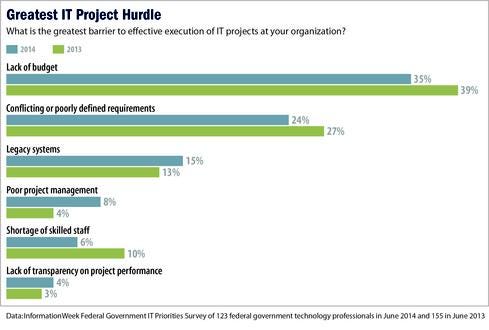
Managers have to take a defense-in-depth approach, embracing the notion that systems are more secure when their various components are protected individually. Reddix says defense in depth should start with two-factor authentication, whereby each user employs security tokens combined with a password or a question/answer to gain access to information. Such a layered security approach makes it impossible to breach an entire system by cracking one password.
At the same time, securing information as it becomes more mobile and "intrinsic to everybody's life" is a growing challenge, Reddix says. As devices proliferate across the government and among consumers, so do the number and complexity of threats. In a mobile security study published last September, the Government Accountability Office reported that the number of variants of malware aimed at mobile devices had risen from about 14,000 to 40,000, or about 185%, in the last year.
Security Comes First
Responses to another question in InformationWeek's 2014 Federal Government IT Priorities Survey reflect federal IT's rising concerns about security. Asked to what degree their agencies are pursuing the government's major IT initiatives, respondents put trusted Internet connections (27%), identity management (20%), and continuous monitoring (13%) in the "very aggressively" category. Continuous monitoring and identity management moved up the list compared with last year's survey, when they were ranked fourth and fifth, respectively.
But the fact that information security ranked ahead of other government IT programs isn't surprising.
"The cyber-security emphasis means that [agencies] are trying to secure everything first and then talk about other things like cloud or continuity of operations," says Augustine Riolo, president of Knowledge Information Solutions in Virginia Beach, Va., whose government customers include the Defense Department, the National Institutes of Health, and NASA.
Continuity of operations planning (COOP) and disaster recovery planning were rated second in importance to security in our survey, with 31% citing COOP as "extremely important." Another 38% put COOP in the "very important" range.
"The whole idea of having backup and disaster recovery is really a function of thinking about how data is made available and the idea of redundancy in storage," Riolo says. Referring to IRS claims that the agency lost thousands of emails connected to politically embattled former IRS official Lois Lerner, all due to a computer crash, Riolo adds: "If they indeed have lost the emails, then the government has a much larger problem dealing with disaster backup and recovery than any of us thought."
Figure 3: 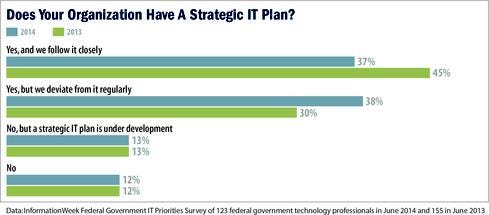
Other IT initiatives that feds and their industry partners rated much lower than security and COOP include interagency collaboration (rated extremely important by 14% of respondents); data records management and shared services (13% each); and data center consolidation, virtualization, IT project management, mobile communications and wireless, PC/laptop upgrades, and mobile device management (12% each). Survey respondents gave all of those areas a "moderately important" rating in the 40% to 50% range.
Where's The Cloud?
One of the federal government's highest-profile IT initiatives, cloud computing and the Obama administration's Cloud First program, placed surprisingly far down the list of priorities in our survey. Only 11% of respondents rated cloud computing initiatives as "extremely important" at their agencies, though 57% placed them in the "moderately important" category. By comparison, 15% rated cloud programs as "extremely important" in last year's survey. Furthermore, only 5% of survey respondents reported that their agency is pursuing the cloud "very aggressively," down from last year's 9%.
When asked specifically about replacing infrastructure with cloud services in the upcoming fiscal year, 54% of respondents reported a current or planned implementation of private or public cloud services (21% private, 13% public, 20% a mix of public and private clouds). However, nearly half, 46%, said their agencies aren't considering cloud deployments in the next fiscal year (compared with 41% in the 2013 survey).
Figure 4: 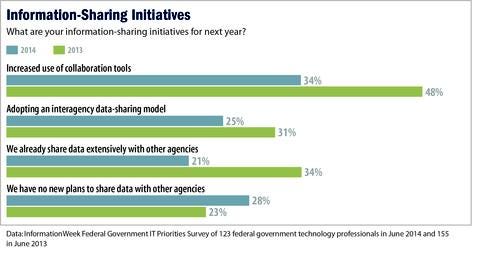
Among those moving ahead with cloud implementations, there's a balance of models and technologies -- 48% of respondents are deploying shared clouds within a government environment, 40% are turning to software-as-a-service, 37% to platform-as-a-service, 34% to cloud service management tools, 32% to hybrid public-private clouds, and 25% to infrastructure-as-a-service.
As for cloud security, 32% of the respondents whose agencies have migrated or plan to migrate to the cloud said their organizations use a cloud service that has been certified under the Federal Risk and Authorization Management Program (FedRAMP), which provides a standardized approach to assessment, authorization, and continuous monitoring of cloud products and services. While 42% of survey respondents said they expect to receive FedRAMP certification within the next six months, 26% said their agencies have no plans to use FedRAMP.
Under Cloud First, started in 2011 by former federal CIO Vivek Kundra, agencies are required to take full advantage of cloud computing to maximize capacity utilization, improve IT flexibility and responsiveness, and minimize costs. But agencies are finding that migrating to the cloud is easier said than done.
One impediment is legacy infrastructure, a jagged landscape of ancient and disparate applications and technologies. Federal agencies "all have some level of systems that they have maintained for many, many years -- original installations of applications that they can't get out of," Riolo says. "As a result, they can't go to the cloud because they don't have applications that the cloud can support."
There's also organizational resistance to change, Reddix says, "a cultural factor within government agencies that says, 'Leave it alone.' They're very hesitant to get into something new, and there's an enormous amount of legacy. There are also vendors that are happy to stay with [operations and maintenance] as consistent dollars."
Still Too Many Data Centers
Indeed, our 2014 Federal Government IT Priorities Survey found that resistance to change is slowing another government-wide IT initiative: data center consolidation, which Kundra established in 2010. In this year's survey, 28% of respondents said cultural resistance is the biggest barrier to their agencies' data center consolidation efforts, up slightly from 26% in the 2013 survey. Other barriers cited this year are technical problems migrating applications (24%), lack of people (18%), lack of a clear vision or leadership (17%), and lack of accurate data center inventory (3%).
Figure 5: 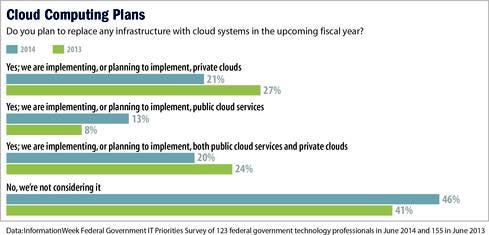
Overall, our survey shows mixed progress. Thirty-nine percent said their agencies have consolidated data centers over the past 12 months, compared with 44% last year, while 23% said they hadn't completed any consolidations in the last year but are planning to this year, up from 18% in our 2013 survey. Twenty-two percent reported no consolidations in the last 12 months.
One survey respondent, a Commerce Department IT capital planning manager, says his department is keeping data center consolidation small scale. "Big-scale data center consolidation is only in the early planning stages," the manager says.
Lack Of Budget … Or Not A Priority?
Among the greatest barriers to executing IT projects at agencies is lack of budget, cited by 35% of survey respondents, down slightly from 39% in 2013. Other barriers include conflicting or poorly defined requirements (cited by 24% this year compared with 27% in 2013), legacy systems (15% compared with 13%), and poor project management (8% against 4%).
Reddix isn't buying the lack of budget excuse. "The government has money -- it's a lack of priority in the budget," he says. "We spend $300 [million] to $400 million on a plane. That's a lot of money. Lack of priority and also the legacy environment are barriers."
Figure 6: 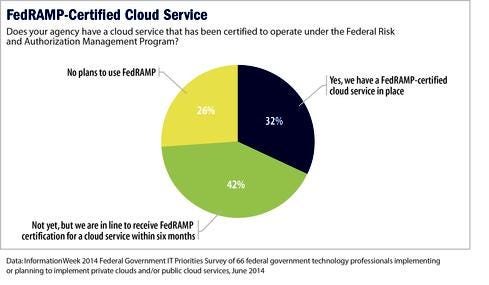
One civilian agency manager agreed that legacy systems are an obstacle to IT effectiveness. "Federal equipment is getting older and older," the manager says. "I am running a Dell OptiPlex 755. A good story would be about the aging equipment for most of the contractors and federal developers." However, the legacy systems problem doesn't apply to everyone at the manager's agency.
"The senior executive types have iPads," he says. "Unbelievable."
Requirements proved to be an issue for a contractor for the US Central Command. "I see military and government employees so focused on missions that they have little time to maintain awareness on IT requirements," the contractor says. "They just expect it to be there when they need it."
Survey respondent Christopher Peschke, a design engineer at HEI Inc., a government subcontractor that manufactures circuit boards and microchips for the Defense Department, says tight agency budgets are making life difficult for contractors. "When you're dealing with government agencies, they generally go with the lowest quote, so you try to eliminate as much overhead as you can," he says. "We have to drive down the price of the quotes to win [contracts]."
On the matter of contracts, only 10% of noncontractor respondents to our survey said their agencies had increased the use of lowest price technically acceptable (LPTA) contracts compared with 12 months ago, while 41% reported that their LPTA use remains about the same compared with last year. Some 18% said LPTA contracts have caused "significantly more" problems and remediation costs.
Collaboration Breakdown?
Only 34% of respondents to our survey see an increase in the use of collaboration tools at their agencies, compared with 48% in 2013. Twenty-five percent are adopting an interagency data-sharing model this year, compared with 31% last year. Twenty-one percent said their agencies already share data with other agencies, and 28% have no new plans to share data in the next year.
Collaboration appears to be mainly within agencies, Riolo says, rather than cross-government. "Take NIH, for example. You may have collaboration between the National Cancer Institute and the [National Heart, Lung, and Blood Institute] within, but you're not going to have collaboration with Commerce or State or anything like that."
We also asked in our survey how comfortable government IT pros are with using open source software. In this year's survey 31% of respondents said they're "very comfortable" using open source, down slightly from 34% last year, and 17% are comfortable with it but don't use it. A hefty 40% said they're not comfortable with open source software.
Figure 7: 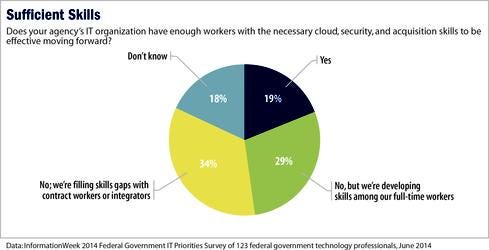
Reddix notes that Whitehouse.gov began running on Drupal, an open source content management system, in 2009. That move was considered a big win for the open source model, he says, but he warned against continued cultural resistance.
"They actually released the code and it saved a lot of money," Reddix says of the White House move. "Using open source, you don't have to reinvent the wheel at every agency or subdepartment. But the culture says, 'I've got my tried and true kind of technology and it's the only thing I know.' "
Innovation Crawl
In general, government IT pros are less bullish than they were last year about tech innovation at their agencies. Only 7% of survey respondents this year cited a "significant" level of IT innovation at their agencies, compared with 14% last year, while 58% cited "moderate" improvement, compared with 57% last year. Nearly a third reported very little innovation at their agencies (3% reported no innovation).
Asked about their agencies' IT efficiency, 6% of survey respondents reported much improvement, 34% somewhat better, 40% the same as before, and 17% less efficient.
Thirty-seven percent of respondents said their agencies have a strategic plan and follow it closely (down from 45% in the 2013 survey), while 38% said they have a plan but deviate from it regularly (up from 30% last year). Reddix attributes the inertia in IT reflected in this year's survey to "innate culture" in government. "If you're looking at a root cause, it would probably be the umbrella culture of the Washington environment itself," he says. "Culture affects everything."
Another survey participant pointed a finger at Washington-centered program control. "Everything must be done by central office," the participant says. "No one outside of D.C. matters."
However, one survey-taker begged to differ, indicating that tech innovation has a place in government: "My agency has made much progress in getting ahead of the IT curve in the past five years."
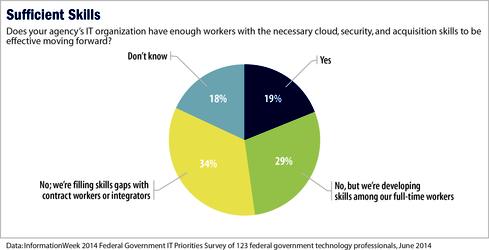
Government agencies continue to struggle to find and keep people with the right IT skills. Nineteen percent of survey respondents said their IT organizations have enough people with the necessary cloud, security, and acquisition skills, while 29% said they lacked sufficient workers but are developing those skills among full-time employees. Another 34% said they lacked skilled workers and are filling gaps with contractors.
Says one survey respondent: "There are still too many dinosaurs in positions for which they don't have qualifications or knowledge pertinent to the decisions they make daily."
Get the August issue of InformationWeek Government.
About the Author(s)
You May Also Like







