A suppressed security paper shines a light on the shortcomings of the cryptography used to protect keyless vehicle access systems.

New York Auto Show: Cool Cars With Hot Tech
New York Auto Show: Cool Cars With Hot Tech (Click image for larger view and slideshow.)
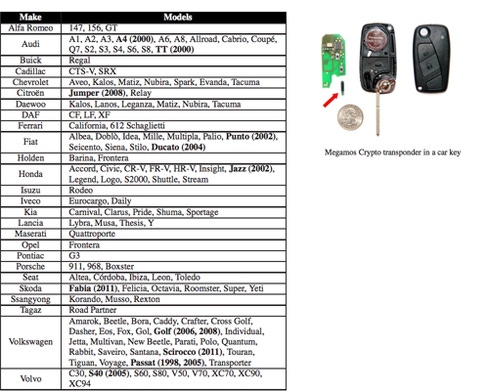
A two-year-old research paper documenting flaws in the Megamos Crypto transponder, used to protect Audi, Fiat, Honda, Volkswagen, Volvo, and other vehicles with keyless ignition systems, demonstrates that you don't need a key to steal a car protected by keyless authentication.
The paper is being presented as part of the 2015 Usenix Security Symposium in Washington, D.C., this week. It was originally scheduled to be presented in 2013, but Thales and Volkswagen, developer of the Megamos Crypto system, sued in the UK to prevent its publication and won an injunction, despite nine months of advance warning from the researchers. The company argued that the publication of the paper could allow sophisticated thieves to bypass protections and steal cars.
That's exactly what the paper's authors, British computer scientist Flavio Garcia and the Dutch researchers Baris Ege and Roel Verdult, say is cause for concern, at least for the car models tested in 2012. "The implications of the attacks presented in this paper are especially serious for those vehicles with keyless ignition," they conclude. "At some point the mechanical key was removed from the vehicle but the cryptographic mechanisms were not strengthened to compensate."
Keyless ignition systems, perversely, have keys. While a keyless vehicle may have a start button instead of a mechanical key port, the electronic fob that authenticates the owner and allows the engine to start relies on a cryptographic key, stored on an RFID chip.
The Megamos Crypto transponder uses a 96-bit key. But it has a variety of flaws, according to the researchers. It lacks a pseudo-random number generator, making it vulnerable to replay attacks, and its internal cipher consists of only 56 bits, among other problems.
It took the researchers all of 30 minutes to recover the 96-bit key from the transponder. A second attack took a bit longer, two and a half hours.
This is not just a problem for the Megamos Crypto transponder. The paper says that there are known attacks for the other widely used immobilizer transponders, specifically DST40, Hitag2, and Keeloq.
Volkswagen did not immediately respond to a request for comment.
In February, the UK's Metropolitan police said that more than 6,000 vehicles last year, representing 42% of thefts of cars and vans, were stolen without the owners' keys. The agency said that while some of those thefts could involve vehicles that had been towed away, the majority of them "appear to be the result of organised criminals using key-programming devices to create duplicate keys for vehicles."
[Read about a summer full of car hacks. ]
Such thefts, however, probably do not involve techniques described in the research paper. As the Metropolitan police point out, keyless vehicles are commonly stolen by breaking into the vehicle, electronically or physically, and using the onboard diagnostic port (OBD) to program a new key.
Such thefts appear to be less common in the US. Last year the US National Insurance Crime Bureau (NICB) warned that thieves were exploting keyless authentication systems to open locked cars using "scanner boxes," to steal personal items.
But Frank Scafidi, spokesperson for the NICB, said in a phone interview that he hasn't seen one report where a car has been stolen by the external hacking of a keyless system. He said there have been some reports of thefts arising from OBD abuse, but not an overwhelming number.
About the Author(s)
You May Also Like







