Government agencies have inconsistently responded to both cyber and non-cyber incidents, a watchdog group says.

Iris Scans: Security Technology In Action
Iris Scans: Security Technology In Action (Click image for larger view.)
Federal agencies need to do a better job handling data breaches. The number of security incidents involving personally identifiable information has more than doubled just in the past four years, a new report by the Government Accountability Office says.
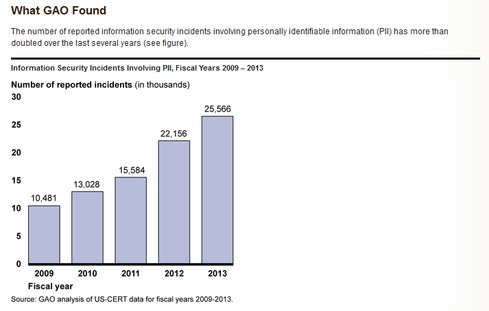
The US government collects large quantities of personally identifiable information, including taxpayer data, census data, Social Security information, and patient health information. But despite agencies' efforts to secure this information, incidents involving personal data -- both cyber and non-cyber -- have skyrocketed from 10,481 in 2009 to 25,566 in 2013, said the federal watchdog agency.
One incident cited in the GAO report took place in July 2013, when hackers stole information like Social Security numbers, birth dates, locations, and bank account numbers on more than 104,000 individuals from a Department of Energy system. Another incident in March 2012 exposed personally identifiable information on 2,300 employees after a laptop computer was stolen from the National Aeronautics and Space Administration.
[Project Interoperability aims to develop tools to help agencies share threat information. Read Feds To Improve Threat Information Sharing.]
The report was presented as testimony by Gregory Wilshusen, the GAO's director of information security, before the Senate Committee on Homeland Security and Governmental Affairs on April 2. "The loss or unauthorized disclosure or alteration of the information residing on federal systems can lead to serious consequences and substantial harm to individuals and the nation," Wilshusen said in his testimony. "Thus it is critical that federal agencies protect their systems and the information on them and respond to data breaches and cyber incidents when they occur."
The GAO used previously published and ongoing work to compile this month's report. In December 2013, it released a study that reviewed eight agencies: the Centers for Medicare and Medicaid Services, Departments of Army and Veterans Affairs, Federal Deposit Insurance Corporation, Federal Reserve Board, Federal Retirement Thrift Investment Board, Internal Revenue Service, and Securities and Exchange Commission. The study concluded that their responses to data breaches were inconsistent and needed improvement.
The selected agencies have since developed breach-response policies and procedures, but they have yet to implement key practices set forth by the Office of Management and Budget and the National Institute of Standards and Technology, the GAO said. The report determined that incomplete OMB guidance contributed to erratic implementation of those security practices. For instance, it's unclear based on that guidance how agencies should use risk levels to decide whether people affected by a breach should be notified.
Of the seven agencies reviewed in the new report -- the FRTIB was excluded -- only the IRS consistently documented both an assigned risk level and how that level was determined for personal information-related data breaches. The Army and IRS were the only two agencies to document the number of affected individuals for each incident. The Army also notified affected individuals for all high-risk breaches, and so did the SEC.
However, none of the seven agencies regularly offered credit monitoring to those affected by breaches. And none of the agencies consistently documented lessons learned from their breach responses, including actions to prevent future incidents and the need for better security controls.
The GAO concluded that agencies must take action to secure the personal information they collect. This includes establishing comprehensive agencywide information security programs and successfully responding to incidents when they happen. The GAO said it will make recommendations to the OMB and the Department of Homeland Security to improve the effectiveness of government-wide cyberincident response activities. A GAO report later expected this spring will take a closer look at federal agencies' ability to respond to cyberincidents.
Cyber-criminals wielding APTs have plenty of innovative techniques to evade network and endpoint defenses. It's scary stuff, and ignorance is definitely not bliss. How to fight back? Think security that's distributed, stratified, and adaptive. Read our Advanced Attacks Demand New Defenses report today (free registration required).
About the Author(s)
You May Also Like







