Take these 4 steps to improve the security of your virtualization infrastructure.

What's the most dangerous threat to your virtualized systems? Hint: it's not the latest zero-day exploit. The most pressing risk is IT staff who have full privileges in these systems.
Take the February 2011 attack by an IT employee who'd been laid off from a pharmaceutical company. The ex- employee logged in remotely and deleted virtual hosts that ran the company's critical applications, including email, financial software, and order tracking. The company sustained about $800,000 in losses from a few keystrokes, the FBI says.
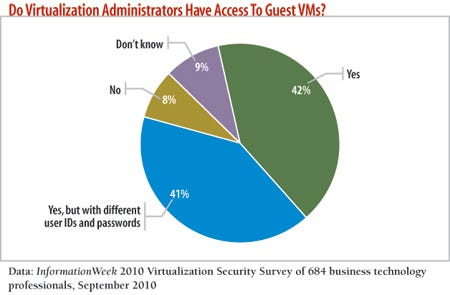
We're not saying your administrators will go rogue, but our September 2010 survey on virtualization security found that access to virtualization systems is fairly widespread: 42% of respondents say administrators have access to guest virtual machines. It only makes sense to take precautions, such as security monitoring, so that one person, whether maliciously or inadvertently, doesn't bring down critical apps and services.
Virtualized systems make it harder to manage risk, but sensible security practices still apply. Here are four steps to help you protect virtual assets and respond to threats and incidents.
1. Secure Layers
Virtual environments are made up of layers, so you'll want to implement security controls at each layer within the virtual architecture, including controls that you already have in your environment. For example, at the virtual switch layer, redirect traffic out to a firewall or an intrusion prevention system to monitor traffic. Alternatively, use a virtual firewall within the VM cluster.
The primary virtual layers to address include the hypervisor and guest operating systems, the virtual network that connects VMs, the physical network, the virtualization management system, and physical storage of VM images.
2. Define And Document
You can't place security controls around elements you don't know are there. Thus, it's vital to have accurate, up-to-date information on your virtual environment. That means being able to identify the components in your virtual infrastructure. Make sure you document the primary functions of these components and their owners and administrators.
It's also critical to understand how data traffic flows through your infrastructure, because the type of data will determine which controls are needed. For example, most companies take extra steps to secure virtual database servers that store critical business data. However, your backups also have copies of this confidential data. Track data flows from start to finish to identify critical areas where additional security measures are needed.
3. Restrict And Separate
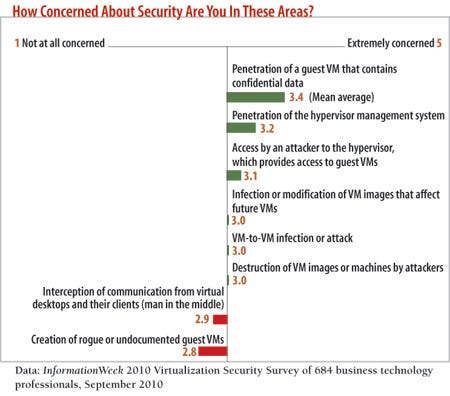
Access control and authorization are core security functions, particularly for virtual environments, where control over a single hypervisor can also mean control over the multiple virtual machines that run on top of that hypervisor. As in the physical world, administrator access to systems and their authorization to perform specific functions should be as specific as possible. Every administrator in your shop doesn't need to be able to spin up, modify, and shut down every virtual server in your data center. Logging is another critical security function. It lets you monitor and track all the activities that take place within the virtual environment.
The management consoles from the major hypervisor vendors provide decent role-based access controls that restrict administrators' permissions to perform basic tasks, and you should take advantage of these capabilities. However, these management consoles don't validate change requests, log all changes, and implement capabilities such as two-factor authentication.
For that, you'll need third-party software from vendors such as HyTrust and Catbird, which provide additional controls, such as change management. With these controls, major changes can't be made to critical systems without authorization from another administrator in addition to the one requesting the change. These third-party tools can also split functions among different IT groups. For instance, the IT security team can be put in charge of managing the logs from the virtualization management console instead of the server administrators. This separation of duties means no single administrator can modify or disable systems undetected.
4. Secure The Virtual Network
The virtual network has the same problems as the physical one, including the potential for man-in-the-middle attacks, in which compromised VMs intercept traffic between other VMs. To prevent these, it's important to take advantage of the security features in your virtual switches. Most virtualization vendors let you set up VLANs that can segment network devices and traffic based on security and management policies.
However, the virtual switch you have in place may lack advanced security and monitoring features of physical switches. For instance, a physical switch lets you create private VLANs, which allow for additional segmentation (think of a VLAN within a VLAN), but many virtual switches don't support this feature. Virtual switches may also lack the ability to provide netflow data, which can be used for performance monitoring and attack detection. Do your homework to see if you need a third-party virtual switch that provides these advanced capabilities.
If you can implement only one of these steps at the outset, focus on access control and separation of duties. Most companies have procedures and tools in place to control access to physical systems, and these can be applied directly to virtual environments. Virtualization's risks and challenges can be countered with common security practices.
About the Author(s)
You May Also Like







