New tool blocks companies from tracking you online, lets you mask sensitive information such as email, phone number, and credit card information.

HP's 3D Future: Sprout Visual Tour
HP's 3D Future: Sprout Visual Tour (Click image for larger view and slideshow.)
In a world of data breaches and websites that track your every move, protecting your personal information isn't easy. That's where Blur comes in. A new tool from online privacy company Abine, Blur lets you browse the Web without being tracked or forced to provide personal information in order to log in or complete transactions.
Blur's three main features include a password manager, a masking feature for sensitive information, and blocking capabilities against targeted ad networks and data collection companies. Abine CEO Rob Shavell said that the company's goals are to keep users safe using simple tools.
"We really believe that the future of protecting your privacy and security online is to stop giving so much information out in the first place," he said. "And the problem hasn't been that people are lazy and don't want to understand how some things work; it's that the software hasn't been easy enough to use. That's what we're aiming to do here."
[Popular social apps may track your every move. Read Location Tracking: 6 Social App Settings To Check.]
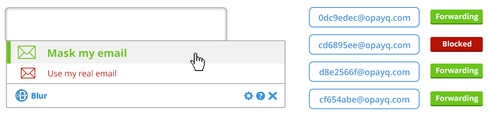
Blur uses a method it calls masking, which creates a new email address, phone number, or credit card to give a website for logins or purchases instead of using your real information.
If you give a site a masked email address and they send you a message, Blur will forward it to your real email address. It works the same way with phone calls: If someone calls your masked phone number, Blur will forward that call to your real phone number. In both cases you still receive those communications -- if you choose -- but without divulging your personal information.
Blur also lets you use masked credit cards -- a unique credit card number that is issued only for the amount of your purchase -- for online transactions.
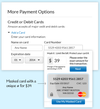
"It's like making an instant gift card for an amount that's used only for that merchant," Shavell explained. Blur's servers then bill your real credit card for the amount of your purchase.
In addition to the masking technology, Blur prevents hundreds of websites, including Facebook, Google, and other data collection companies and targeted ad networks, from tracking your online browsing habits. You can also use Blur as a password manager to save your login and password details, which are encrypted and synced to all your devices.
Shavell said that Blur will remain ad-free and without conflicts of interest, relying instead on subscriptions to make money.
"People ask us, 'How can we trust you guys?' And we say you have to look at how the company makes money," Shavell said. "We don't have conflicts of interest, we don't have advertising, and have been very purposeful in setting up a business where the more privacy you want, the more money we make."
Blur offers both free and paid versions of the tool. The free version includes tracker blocking, masked emails, and the password manager feature. The paid version includes those features, plus masked credit cards and phone numbers, backup and sync options, and user support. Subscription options include $39 billed yearly; $59 for two years; or $79 for three years.
To be fully protected, you will need to download the add-on or app for every device you use. If you opt for the paid version of Blur, you'll be charged only once regardless of how many devices use it.
Considering how prevalent third-party attacks are, we need to ask hard questions about how partners and suppliers are safeguarding systems and data. In the Partners' Role In Perimeter Security report, we'll discuss concrete strategies such as setting standards that third-party providers must meet to keep your business, conducting in-depth risk assessments -- and ensuring that your network has controls in place to protect data in case these defenses fail (free registration required).
About the Author(s)
You May Also Like







