Amazon has quietly added support for multi-factor authentication for customers using its ecommerce site in the US. Why would the company do this now?

Insider Threats: 10 Ways To Protect Your Data
Insider Threats: 10 Ways To Protect Your Data (Click image for larger view and slideshow.)
With little fanfare and about as far under the radar as you can go, Amazon added multi-factor authentication (MFA) to its e-commerce website.
The news broke this week, and it came as a bit of an early Black Friday surprise for many. Richard Lawler, a senior editor at Engadget, ferreted out the information and received confirmation from an Amazon security engineer that it has been in beta testing and rolled out quietly about two weeks ago. (Editor's note: This article was updated on Nov. 20 to reflect that the engineer originally quoted by Engadget cited by InformationWeek was not an authorized spokesperson for the company.)
The MFA seems to be for the US only at this point. Responses on Engadget and Twitter indicate that MFA wasn't showing up in Germany or Canada.
[Read how the Paris attacks have renewed the encryption debate in the US.]
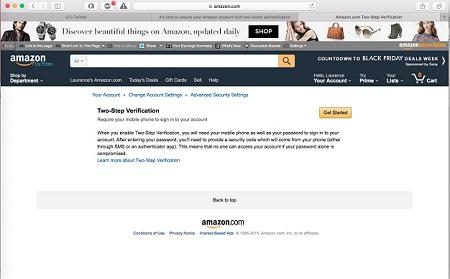
If you're in the US, here's how to create the MFA on your Amazon account: Open your account menu on a merchandise page then click the Change Account Settings on the resulting page. The next page lists your specific account settings. By then clicking on Advanced Security Setting, the MFA process will begin on the page that is opened.
Outside of a general concern about security (What company large or small is not concerned about security these days?), it's not clear why Amazon decided now was the time to start offering MFA options for customers. One reason could be the impending holiday shopping season. The never-ending onslaught of breaches and data theft is probably another.
The website Twofactorauth.org shows that the MFA trend is being picked up by more and more companies and technology services, so Amazon is not alone in going down this road.
If Amazon had something more specific in mind, it's not saying. The company did not respond to questions on Thursday.
However, Amazon is currently offering MFA in another part of the company, and that could be the reason for bringing it to its main commerce site. Amazon has used multi-factor authentication in its Amazon Web Services cloud computing platform since 2009. It added virtual devices to the MFA mix in 2013.
MFA typically requires something you are (your user name), something you know (your password), and something you have (a separate device from the one you're using to access the site or app). For example, with MFA enabled on AWS, a user signs in to an AWS website and is then prompted for a user name and password (something the person is, and something he or she knows), as well as for an authentication code from an AWS-supported MFA device (something the individual has).
Various types of devices can be used for the AWS MFA service. It can be a hardware key fob or a hardware card device. It can also be a smartphone using either a TOTP-compliant MFA application like Google's Authenticator, or a text message sent to the phone.
While Amazon said that the text-message MFA option for its commerce site is currently "in preview," immediate sign-up for it is available. This kind of MFA may not be the most secure, since it introduces the wireless carrier as a possible point of failure.
**New deadline of Dec. 18, 2015** Be a part of the prestigious InformationWeek Elite 100! Time is running out to submit your company's application by Dec. 18, 2015. Go to our 2016 registration page: InformationWeek's Elite 100 list for 2016.
About the Author(s)
You May Also Like







